The Battle Continues
Examining the Most Common Adversary Tactics based on The Red Report 2023 by Picus security.
Victor Monga
3/16/20236 min read

Predict the future by creating it












Are You Prepared to Defend Against the Top 10 Most Prevalent Adversary Techniques?
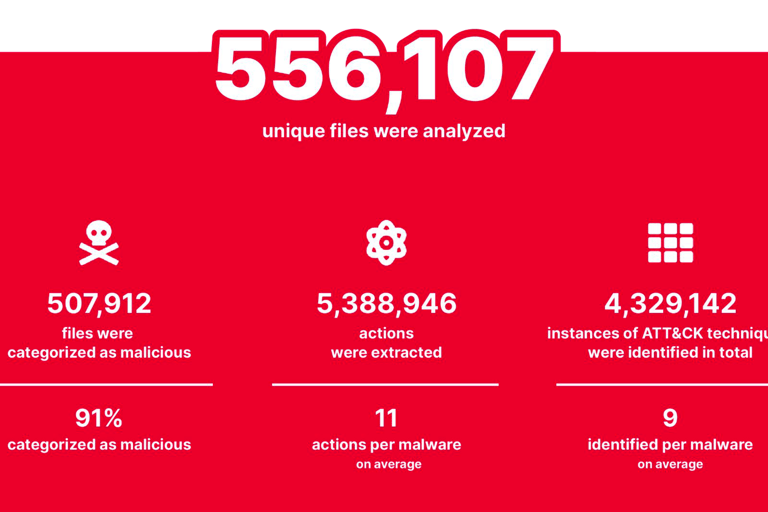
The latest Red Report highlights a significant increase in attackers using malware for Lateral Movement, which involves moving from one compromised system to another in a network to further their objectives. The report identifies three new techniques in this year's top ten list that are primarily used for Lateral Movement, along with two prevalent techniques, Command and Scripting Interpreter and OS Credential Dumping, that aid in the execution of commands on remote systems and obtaining account credentials. The increase in such techniques highlights the importance of improving threat prevention and detection measures both inside and outside networks.
#1 T1059
Command and Scripting Interpreter
Command and scripting interpreters, such as PowerShell, VBScript, and Unix shells, provide a powerful tool for legitimate users to automate and simplify operational tasks. However, adversaries can exploit these interpreters to execute malicious code on local and remote systems during their attack campaigns. As they are built-in tools, adversaries can use them stealthily to bypass weak process monitoring mechanisms and carry out malicious activities. The T1059 Command and Scripting Interpreter technique can be used to achieve various tactics in the MITRE ATT&CK framework, including Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Command and Control, and Exfiltration etc. This highlights the importance of implementing strong security controls to detect and prevent malicious use of command and scripting interpreters.

#2 T1003
OS Credential Dumping
To prevent OS Credential Dumping, security teams can implement measures such as:
Enforcing strong password policies and regularly changing passwords
Limiting administrative privileges to only those who require them
Using multi-factor authentication to reduce the effectiveness of stolen credentials
Keeping operating systems and software up to date with the latest security patches
Monitoring and logging system events to detect potential credential dumping activities
Using endpoint detection and response (EDR) solutions that can identify and respond to credential dumping activities in real-time.

The Red Report 2023 reveals that OS Credential Dumping has become the second most prevalent technique used by adversaries to obtain account credentials, highlighting the need for improved security measures.
#3 T1486
Data Encrypted for Impact
Data Encrypted for Impact is a highly effective technique used by adversaries to disrupt businesses through malicious use of encryption. This technique is increasingly prevalent, with the Red Report 2023 ranking it as the third most common adversary technique. Adversaries use advanced encryption algorithms to render victims' data unusable, and in ransomware attacks, they demand payment in exchange for the decryption key. To mitigate the impact of this technique, organizations may implement the following measures:
Regularly back up critical data and store it in an offline or offsite location
Use strong encryption algorithms and secure key management practices
Implement multi-factor authentication for privileged accounts
Keep software and security systems up-to-date with the latest patches and updates
Train employees on how to identify and avoid phishing attacks and other social engineering tactics
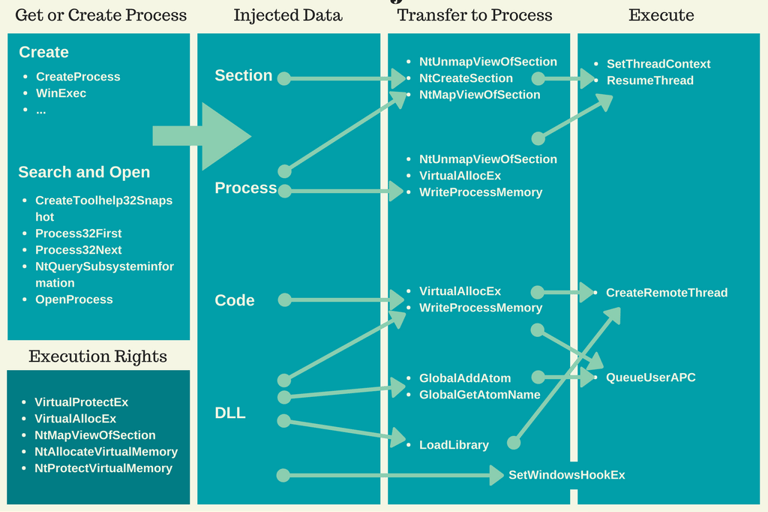
#4 T1055
Process Injection
Process injection is a common technique used by adversaries to achieve an increased level of stealthiness, persistence, and privilege on a victim's system. The T1055 Process Injection technique remains in the top five of Top Ten attack techniques. Adversaries may use Process Injection for various purposes, such as evading detection, persisting on a system, or gaining access to the system's resources. According to a Ponemon Institute report, "The Cyber Resilient Organization: Learning to Thrive Against Threats," 68% of organizations experienced a successful attack involving the use of fileless malware or other memory-based attacks, including process injection.
#5 T1082
System Information Discovery
Recently, the Conti ransomware group used System Information Discovery to gather information on victims' networks before deploying ransomware. They used a tool called "SharpChisel" to collect data such as user credentials, network topology, and system details. In another incident, the LockBit ransomware group used a tool called "InternalMonologue" to gather system information from compromised systems before encrypting files. System Information Discovery was also used in the SolarWinds supply chain attack to collect data about the compromised systems, including network configuration and installed software.


#6 T1021
Remote Services
Remote services are important for IT administration because they enable remote access and management of systems, making it easier to troubleshoot issues, perform maintenance, and provide support. However, these services can also pose a danger to security because they can be exploited by adversaries to gain unauthorized access to systems and networks.
To detect anomalies of remote services, it is important to monitor for unusual login attempts, such as failed login attempts or login attempts from unusual locations or IP addresses. It is also important to monitor for unusual activity within remote sessions, such as the execution of unusual commands or the transfer of large amounts of data. Network segmentation and access controls can also help to limit the exposure of remote services and reduce the risk of unauthorized access.

#7 T1047
Windows Management Instrumentation
According to The Red Report, "adversaries abuse the extensive capabilities of WMI to execute malicious commands and payloads in compromised Windows hosts." The report also notes that although PowerShell has largely replaced WMIC for WMI in newer Windows versions, older versions of Windows still use WMIC, and malicious payloads that use WMIC are still used in attacks. SANS has published several articles on using WMI for defense cybersecurity purposes, including "Finding the Needle in the Haystack: Detecting Malicious PowerShell Through WMI Events" and "Defending Against Malicious PowerShell Attacks with Windows Event Logging."

#8 T1053
Scheduled Task/Job
According to security leaders, scheduled tasks are often used for malicious purposes such as remote code execution, persistence, and privilege escalation. Adversaries can use scheduled tasks to maintain their foothold on a system and perform malicious activities even if their initial access is discovered and blocked. They can also evade detection by running their malicious code at times when the system is less likely to be monitored. To defend against this technique, security leaders recommends monitoring scheduled tasks and looking for unusual or suspicious activity. As they note, "Tracking the execution of scheduled tasks can be a powerful way to detect suspicious activity that would not otherwise be apparent."


#9 T1497
Virtualization/Sandbox Evasion
Virtualization and sandboxing are common tools used by security researchers to study malware in a safe and controlled environment. However, malware developers often design their malware with anti-virtualization or anti-sandboxing capabilities to detect and evade such environments, making it harder for researchers to understand the malware and develop effective countermeasures. According to a report by Carbon Black, "75% of malware can detect when it's in a virtual machine or sandbox, and then change its behavior to evade detection." This highlights the importance of constantly evolving and improving sandboxing and virtualization techniques to stay ahead of malware developers.


#10 T1018
Remote System Discovery
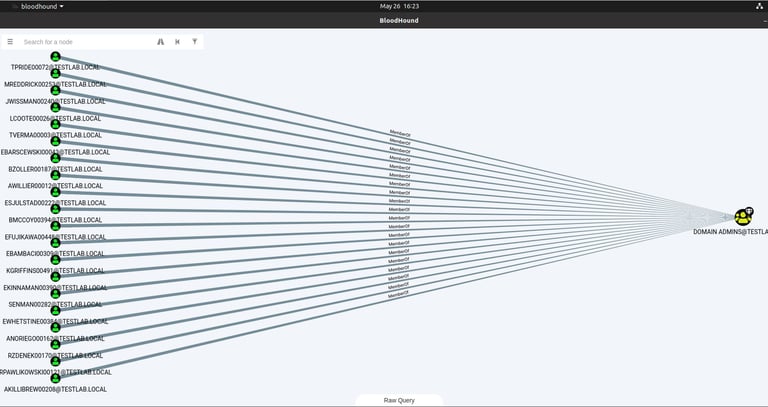
Adversaries use Remote System Discovery to identify other hosts and networks they can pivot to from the compromised initial system. This technique made this year's top ten most prevalent ATT&CK techniques list. According to the MITRE ATT&CK framework, adversaries use native commands and custom tools to exercise this technique, and many operating systems have native commands and tools for networking that allow users to discover other hosts, networks, and services in their environment. Adversaries leverage these built-in utilities to discover remote systems and services. "Adversaries look for remote hosts and networks after gaining initial access to victim environment. Discovering remote hosts and networks potentially opens up a whole new world of attack surfaces that can be exploited for adversaries' objectives. Since advanced cyber attacks almost always involve multiple hosts and networks, Remote System Discovery has made this year's top ten most prevalent ATT&CK techniques list."
Subscribe to latest announcements
Copyright © 2025 Virtually Testing. All rights reserved.




