VTF Webinar
Expert-led insights and hands-on learning opportunities that will set you on the path to success.
Unlock new knowledge with the next VTF webinar.
Expert Insights and Certificate!
Join VTF Webinar and Get Insider Tips from Industry Experts!
Don't miss the opportunity to learn from industry professionals and gain valuable insights into the world of cybersecurity! Sign up for the VTF webinar now and receive a certificate of participation upon completion. This webinar is designed to help you stay ahead of the game in the ever-evolving field of cybersecurity. With interactive presentations, engaging discussions, and real-life case studies, you will be able to deepen your understanding of current trends and best practices in the industry. The VTF webinar is the perfect platform to expand your network and connect with peers from all over the world. Don't wait any longer, sign up now and take the first step towards your professional growth and success!
Discover the Future of Cybersecurity
Join the revolution in the world of cybersecurity and gain insights from industry professionals! Sign up for our VTF webinars and receive a certificate of participation. Choose your preferred platform - whether it be YouTube, Facebook, or LinkedIn, we've got you covered. Don't miss out on this opportunity to enhance your knowledge and skills in the field of cybersecurity. Register now!



Experience the Convenience of VTF Webinars: Watch Anytime, Anywhere on Your Favorite Platform 📱💻
VTF webinars are streamed LIVE on all major social media platforms and can be accessed on-demand once released
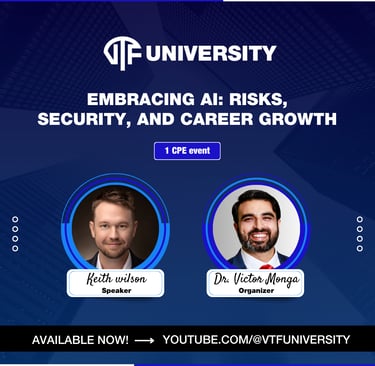
Embracing AI: Risks, Security, and Career Growth
Understanding AI Security Risks – Explore how AI introduces new cybersecurity threats, including data poisoning, model theft, and overreliance on AI-generated outputs.
Key AI Security Frameworks – Learn about NIST AI RMF, OWASP AI Top 10, MITRE ATLAS, and how they shape AI security best practices.
The Future of AI in Cybersecurity – Discuss how AI is transforming cybersecurity operations, from threat detection to adversarial testing.
Career Growth in AI & Security – Discover how security professionals can upskill, embrace AI-driven tools, and stay competitive in the evolving job market.
Responsible AI Use & Implementation – Learn best practices for integrating AI into security workflows while mitigating risks and ensuring accuracy.
Claim your digital certificate
Application Security Fundamentals
Application Security: Essential for protecting sensitive data from threats, ensuring that applications are safe throughout their lifecycle.
API Security: Critical for safeguarding interfaces between applications, preventing unauthorized access and data breaches.
Importance in SDLC: Integrating security in the Software Development Life Cycle (SDLC) helps identify vulnerabilities early, reducing risks and costs associated with late-stage fixes.
CI/CD Pipeline: Continuous Integration and Continuous Deployment streamline development, making it vital to embed security checks to catch issues before production.
Security in CI/CD: Embedding security practices within the CI/CD pipeline ensures that each software release is not only functional but also secure, maintaining trust and compliance.
Claim your certificate upon completion of the webinar!
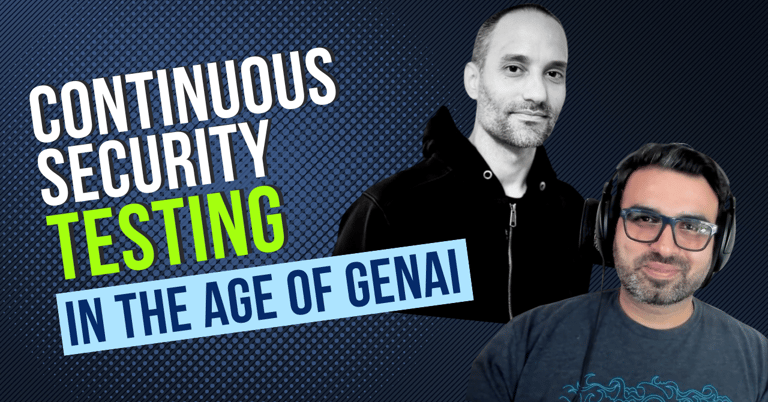
Continuous Security Testing in the age of GenAI
The Evolution of Security Testing: From the early days of penetration testing in the 1990s. The rise of red teaming and breach and attack simulation (BAS). The emergence of automated adversary emulation and CST.
GenAI's Disruption in Cybersecurity: The challenges and opportunities presented by GenAI in 2023-2024. The concept of "Artificial Intelligence Trauma" and its impact on security teams. Differentiating between data that can be generated and data that needs to be accessed.
Claim your certificate upon completion of the webinar!
Attackers know more about your assets than you do; what does that tell you?"
Application Security Fundamentals
Application Security: Essential for protecting sensitive data from threats, ensuring that applications are safe throughout their lifecycle.
API Security: Critical for safeguarding interfaces between applications, preventing unauthorized access and data breaches.
Importance in SDLC: Integrating security in the Software Development Life Cycle (SDLC) helps identify vulnerabilities early, reducing risks and costs associated with late-stage fixes.
CI/CD Pipeline: Continuous Integration and Continuous Deployment streamline development, making it vital to embed security checks to catch issues before production.
Security in CI/CD: Embedding security practices within the CI/CD pipeline ensures that each software release is not only functional but also secure, maintaining trust and compliance.
Claim your certificate upon completion of the webinar!
Autonomous & Automated Security Validation
In an era where digital threats evolve at an unprecedented pace, the need for robust, dynamic security measures has never been more critical.
Introduction to Autonomous Security Systems: Understand the fundamentals of autonomous security and how it differs from traditional security measures.
The Role of Automation in Security Validation: Explore how automated processes are revolutionizing the identification and mitigation of vulnerabilities.
Real-world Applications and Case Studies: Learn from real-world implementations and see how leading organizations are benefiting from autonomous and automated security validation.
Emerging Technologies and Trends: Get insights into the latest technologies shaping the future of cybersecurity, including AI and machine learning applications.
Interactive Q&A Session: Have your questions answered by our panel of experts.
This webinar is designed for cybersecurity professionals, IT managers, and anyone passionate about safeguarding digital assets in the most efficient and effective way possible.
Claim your certificate upon completion of the webinar!
The Art of Protection: Mastering AWS Security Strategies and Tactics
In this webinar, we will explore the art of protecting your AWS environment through mastering security strategies and tactics. Join our expert panelists as they share their insights on best practices for securing your AWS infrastructure, protecting your data, and mitigating risks. Learn about the latest security tools and techniques, and discover how to optimize your security posture for the cloud.
Whether you are an AWS security veteran or just starting out, this webinar will provide valuable insights into the art of protection. Don't miss this opportunity to master AWS security!
February 26
Claim your certificate upon completion of the webinar!

Bridge the gaps proactively with purple teaming
Purple teaming is a proactive way to bridge the gaps in an organization's cyber defense strategy. According to Picus Security, "it’s no longer enough to simply put out fires - businesses need to find a way to reduce the risk of those fires ever starting." With this approach, security professionals on both the red (attackers) and blue (defenders) teams work together to identify weaknesses and enhance defenses.
Picus Security emphasizes the importance of this collaboration: "The goal of purple teaming is to increase overall security posture, shorten response times, improve detection accuracy, and improve the incident response process." By bringing together offensive and defensive tactics, organizations can better protect themselves from cyber threats and stay ahead of the constantly evolving threat landscape.
February 26






Claim Your Certificate:
Having trouble viewing the embed form?
Click - https://certificateform.givemycertificate.com/f/b13f947a-ddcf-46ee-91ab-2e695fe790ab
What is API security?
API security is an essential aspect of cybersecurity as APIs are widely used to transfer data between different applications and systems. As a result, they can also become a potential entry point for attackers to gain access to sensitive information. Learning about API security is crucial for anyone trying to break into the cybersecurity industry as it helps understand the potential risks and vulnerabilities associated with APIs and the measures that can be taken to mitigate them. With the increasing use of APIs in today's digital landscape, understanding API security has become a must-have skill for cybersecurity professionals, making it a valuable investment for anyone who wants to pursue a career in this field.
Claim Your Certificate:
Having trouble viewing the embed form?
Click - https://certificateform.givemycertificate.com/f/bb4796a6-89cd-49a8-9371-a35c959c1fe9
Subscribe to latest announcements
Copyright © 2025 Virtually Testing. All rights reserved.